Local Storage seems to be disabled in your browser.
For the best experience on our site, be sure to turn on Local Storage in your browser.
Wubinworks Tech Blog
-
July 01, 2025 30
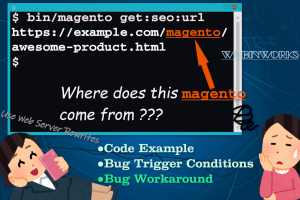
In an internal test case, we found a strange behavior that when trying to build URL in custom CLI commands, the URL sometimes contains an unexpected
magentoin its URI part. In this blog, let's examine... -
March 09, 2025 131
Check whether your Magento store is affected by CVE-2024-34102(a.k.a Cosmic Sting, CVSS Score: 9.8) within 20 seconds. Alternatively, you can check if the applied patch works. Simply input your store's...
-
February 10, 2025 110
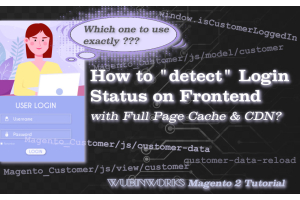
Sometimes we need to "detect"(check) the customer's login status and do something. For instance, display a coupon code to logged in customers only. Things become complicated when Full Page Cache(incl...
-
January 23, 2025 57
Magento supports multiple payment methods and you can even develop your own payment method. This is a big plus as store owners can fully control the last and the most important step of checkout process...
-
December 31, 2024 84
As illustrated in the concept image, we got a request from our client that he wants to use the built-in Admin Grid filter feature to search entries that has empty field. To be more specific in his situation...
-
December 19, 2024 104
Class
\Magento\Framework\Xml\Securityin Magento 2 framework is intended to prevent XXE and itsscanmethod can detect entities in XML input, by design. However, we found a way to bypass thescanmethod... -
December 17, 2024 71
Magento 2 uses "Scoped configuration" to adopt multiple stores setup. Configuration value has a fallback mechanism and the "default value" is stored in
etc/config.xml. In most cases, we just make use... -
December 07, 2024 294
The encryption key in Magento is used to encrypt sensitive data such as API credentials, and most important thing, the Admin WebAPI Token is issued by this key. We need to rotate it if the key is leaked...
-
December 02, 2024 100
Starting from Magento 2.4.7, the encryption key has a new format and the key length is increased to 256-bit. We will demonstrate the key generation process and after reading this blog, you should be able...
-
September 12, 2024 225
How to fix CVE-2024-34102 -- a CVSS Score 9.8(Critical) and RCE possible vulnerability? Upgrade Magento to greater than 2.4.7-p1 is the best solution, but sometimes this could not be done in a few days...