Local Storage seems to be disabled in your browser.
For the best experience on our site, be sure to turn on Local Storage in your browser.
CVE-2024-34102 Cosmic Sting Online Checker
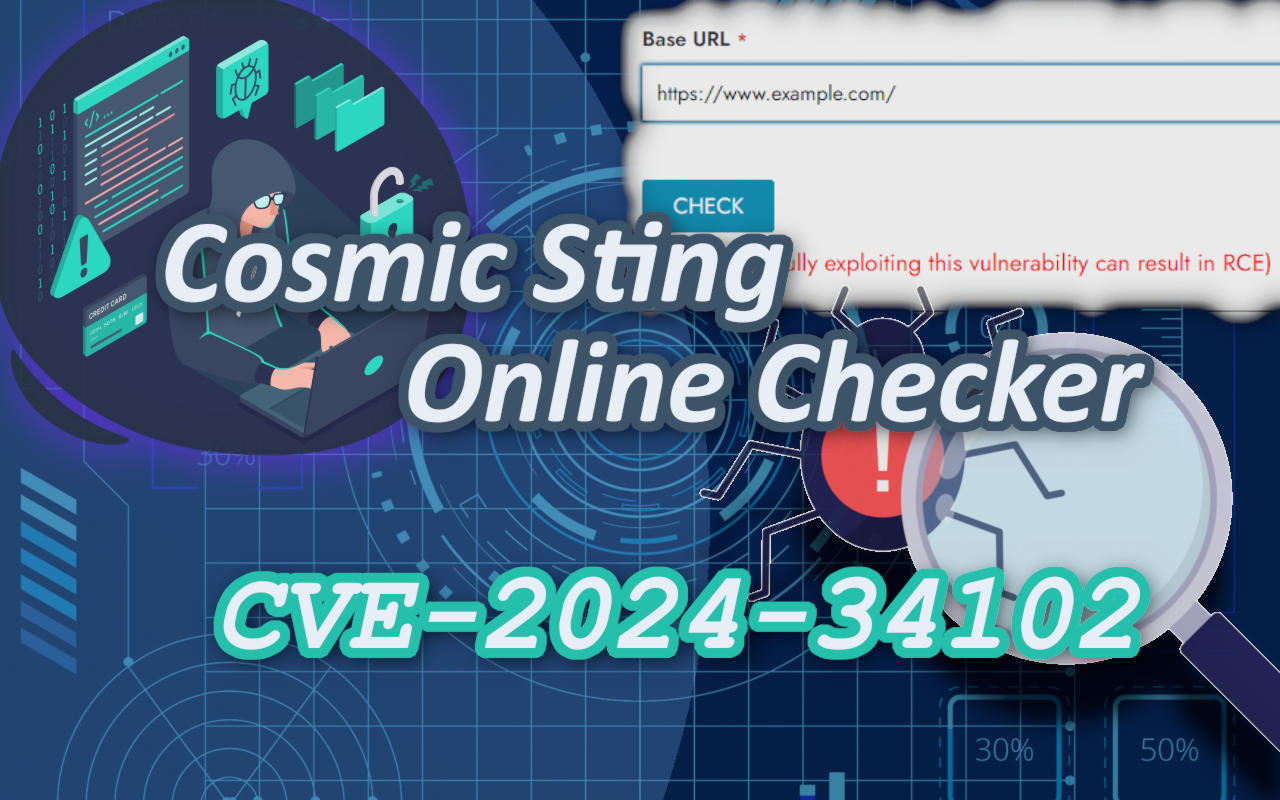
Check whether your Magento store is affected by CVE-2024-34102(a.k.a Cosmic Sting) within 20 seconds. Alternatively, you can check if the applied patch works. Simply input your store's Base URL.
CVE-2024-34102's CVSS Score: 9.8 CRITICAL
Tips
- Base URL of your store is at
Admin Panel > Stores > Configuration > General > Web > Base URLs (Secure) > Secure Base URL. - Only check the websites owned by you or you are authorized by the store owner to perform the check.
- Your website must be public accessible.
- Possible result:
PASS!,FAIL!,Other notice. - Only supports
httpsprotocol for security consideration(So the Base URL must start withhttps). - If your website has Basic Authentication enabled, typically a staging environment, there is way to check without disabling the Basic Authentication. Please contact us.
- Don't hesitate to contact us if you have doubts on the result or have a special Base URL or have other difficulties with checking your website.
Valid Base URL
- ✓ https://www.example.com/
- ✓ https://www.example.com
Tailing slash is optional - ✓ https://www.example.com/some/path
- ✓ https://www.example.com/some/path/
- ✗ https://www.example.com/some-product.html
- ✗ http://www.example.com
httpprotocol is not supported, usehttpsinstead - ✗ https://www.example.com:3443
Specifyingportis not allowed - ✗ https://username:password@www.example.com
userinfois not allowed
But there is another way if your website has Basic Authentication
Patch
wubinworks/module-cosmic-sting-patch
Share This Tool
If you found this tool useful, please share it!

Share on Facebook

Share on X

Share on Pinterest

Share on LinkedIn
Related Posts
Related Service & Extension
Categories
-
Tech
(12)
- How to (8)
- Bug (1)
- How It Works (3)
- Security (6)
-
Customization
(2)
- Admin (1)
Recent Posts
Tags
Magento 2
security
CVE-2034-34102
Cosmic Sting
Customization
Development
Bug
Cache
CDN
Full Page Cache
cve
WebAPI
How to
XXE
security tool
CosmicSting
Performance
Varnish
How It Works
encryption key
Knockout.js
Javascript
Frontend
Block Cache
Cache Lifetime
Layout Cache
FPC
X-Magento-Tags
ESI
Block Tags
IdentityInterface
Cache Purging
TTL
attack
defend
JWT
Authentication
key rotation
token
config.xml
ModularConfigSource
xml
framework
Admin Grid
Filter
UI Component
Search Criteria
SQL
Checkout
Payment Method