Local Storage seems to be disabled in your browser.
For the best experience on our site, be sure to turn on Local Storage in your browser.
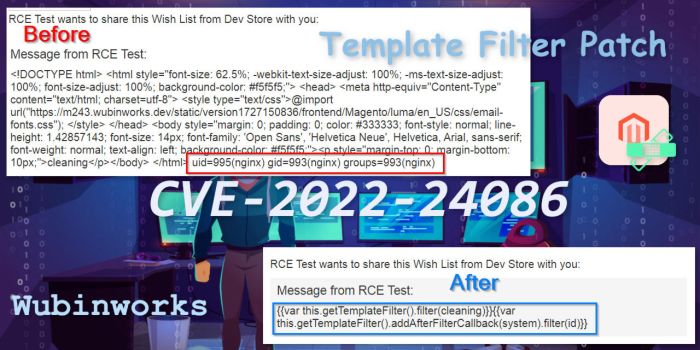
Magento2 CVE-2022-24086 CVE-2022-24087 Template Filter Patch
Magento 2 patch for CVE-2022-24086, CVE-2022-24087. Fix the RCE vulnerability and related bugs by performing deep template variable escaping. If you cannot upgrade Magento or cannot apply the official patches, try this one.
Magento 2 Template Filter Patch for CVE-2022-24086, CVE-2022-24087
Magento 2 patch for CVE-2022-24086, CVE-2022-24087. Fix the RCE vulnerability and related bugs by performing deep template variable escaping. If you cannot upgrade Magento or cannot apply the official patches, try this one.
Background
CVE-2022-24086(with CVE-2022-24087) was discovered in the beginning of 2022.
Affected Magento Versions
- 2.3 series: <=2.3.7-p2
- 2.4 series: <=2.4.3-p1
Affected stores come with this Remote Code Execution(RCE) vulnerability without workaround. 2 official isolated patches were released on February 2022.
However, even in late 2024, we are still receiving consultations regarding this issue and their hacked stores were identified that this vulnerability was exploited. Observed attacks were performed by inputting a string that contains template directive. Typically by making use of the checkout process, actions that can trigger an email sending with user controllable fields, etc.
We make this patch due to this widespread attack and some stores still having difficulties to upgrade to unaffected versions or apply the 2 official patches.
While making this patch as an extension, we keep compatibility in mind. It is mainly tested on Magento 2.4 series.
Features
- Fixed the RCE caused by malicious user data(user input)
- Fixed an Unintended User Data Parsing Bug
- Maintains compatibility as much as possible for old templates(see Template Compatibility Section below)
Template Compatibility
Although the official documentation says "methods can no longer be called from variables from either the var directive or when used as parameters", but as we confirmed, even in the latest version(2.4.7-p3), calling "Getter" method on Data Object and calling getUrl method on Email Template Object(\Magento\Email\Model\AbstractTemplate) are still allowed.
This patch(extension) also keeps the above features. So {{var data_object.something}} and {{var data_object.getSomething()}} are both OK and equivalent.
getUrl example:
{{var this.getUrl($store,'route_id/controller/action',[_query:[param1:$obj.param1,param2:$obj.param2],_nosid:1])}}In summary, after installing this extension:
- Objects which are not
\Magento\Framework\DataObjector its child instance cannot be accessed - Only "Getter" methods are allowed on
\Magento\Framework\DataObjectand its child instances getUrlmethod is only working onthis
Technical Info
Official Approach
>=2.4.3-p2
Removed LegacyResolver to stop the RCE.
>=2.4.4-p2 || >=2.4.5-p1
Introduced "deferred directive with signature" for child template. We are unsure if it has any security enhancement.
Latest(2.4.7-p3)
Still has an unfixed bug(#39353).
Our Approach
Use "deep template variable escaping" before the template filtering process. LegacyResolver will only receive escaped user data and hence can be kept.
Requirements
Magento 2.3 or 2.4
Installation
composer require wubinworks/module-template-filter-patch
♥
If you like this extension or this extension helped you, please ★star☆ this repository.
You may also like:
Magento 2 patch for CVE-2024-34102(aka Cosmic Sting)
Magento 2 Enhanced XML Security
Magento 2 Encryption Key Manager CLI
Magento 2 JWT Authentication Patch
Magento 2 Disable Customer Change Email Extension
Magento 2 Disable Customer Extension
Extension Support
Most Requested Services
- Extension installation or upgrade
- Configuration tweaking
- Add a custom feature to extension
- Resolve extension conflict
For more service details, please refer to Magento Technical Support Service.
Note we require credentials having proper privilege to access your store Admin Panel and code base. This also includes the privilege to restart system services.
We can use git and it is recommended to use git.
Source Code
https://github.com/wubinworks/magento2-template-filter-patch
100% FREE and 100% Open Code. No registration required.
Installation
composer require wubinworks/module-template-filter-patch
License
- OSL-3.0 License